What is Ethical Hacking? A Complete Beginner’s Guide for 2025

The best defense is a good offense.” In cybersecurity, this means fighting hackers with hackers—ethical ones!
Have you ever wondered how companies defend themselves against massive cyberattacks? The answer often lies in the hands of ethical hackers. These digital warriors use their skills for good—protecting data, testing systems, and outsmarting cybercriminals before damage is done.
In this ultimate guide, you’ll learn what ethical hacking is, how it began, and how you can rise to the top of this booming field in 2025. Let’s dive in.
Table of Contents
ToggleWhat is Ethical Hacking?
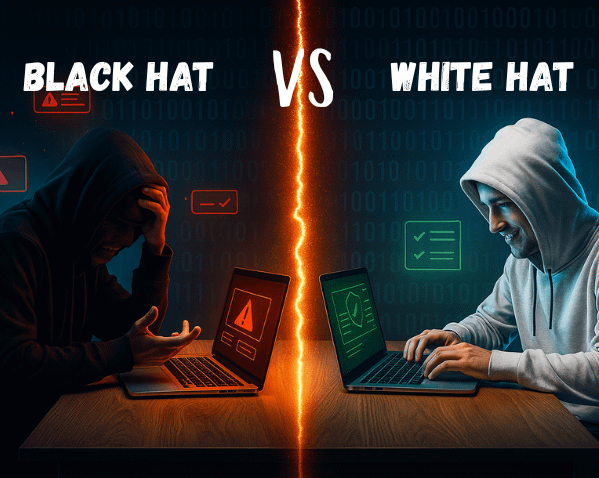
Ethical hacking is the authorized process of probing systems, networks, and applications for vulnerabilities that malicious hackers could exploit. Also known as “white-hat hacking,” it helps organizations identify weak points before bad actors can abuse them. Ethical hackers are hired to think like attackers, but act with integrity, helping businesses strengthen their defenses.
Ethical hacking differs from malicious hacking in three major ways: it is conducted with permission, it is done for defensive purposes, and it follows a structured methodology. Industry-standard frameworks like the Penetration Testing Execution Standard (PTES) guide how ethical hackers approach systems, ensuring thorough and responsible assessments.
Learn more from the U.S. Cybersecurity & Infrastructure Security Agency (CISA).
A Brief History of Hacking (And Why It Matters)
To understand ethical hacking, we need to examine where hacking originated. In the 1960s and 70s, hackers at MIT were simply curious programmers pushing technical boundaries. Hacking meant clever coding and creative problem-solving.
By the 1980s, the term took a darker turn. Individuals like Kevin Mitnick became infamous for unauthorized access and high-profile cybercrimes. Governments began tightening laws, and hacking became synonymous with illegality.
Then came the rise of white-hat hacking. Companies began to realize that they needed hackers to beat hackers. This gave birth to ethical hacking as a legitimate and necessary career. Platforms like HackerOne and Bugcrowd now reward ethical hackers for discovering vulnerabilities and reporting them responsibly.
The Role of an Ethical Hacker
Ethical hackers simulate the mindset of malicious attackers to expose system flaws. Their job is to find security gaps before real hackers do. They conduct penetration tests, analyze systems, report findings, and help organizations implement stronger security measures.
The tools they use and the processes they follow often align with the OWASP Top 10 vulnerabilities and the NIST Cybersecurity Framework. Ethical hackers can work in-house, for cybersecurity consultancies, or as freelance bounty hunters.
They are essential in today’s threat-filled digital environment, acting as offensive security professionals with a mission to defend.
Key Skills Needed to Become an Ethical Hacker
To thrive as an ethical hacker, you need both hard and soft skills. On the technical side, you’ll need a deep understanding of networking, operating systems like Linux, programming languages like Python, and familiarity with cybersecurity protocols.
But that’s not all. You’ll also need analytical thinking, creativity, problem-solving ability, and strong ethical principles. These soft skills enable hackers to think like attackers and act with integrity.
Build your knowledge with platforms like Cisco NetAcad and Kali.org.
Top Tools Used by Ethical Hackers
Ethical hackers rely on a powerful suite of tools to do their jobs. These tools simulate attacks, analyze systems, and exploit vulnerabilities in a controlled, lawful environment.
Nmap helps map networks and detect open ports.
Wireshark is used to analyze packets.
Metasploit is a popular framework for running exploits.
Burp Suite is essential for web vulnerability testing.
John the Ripper is a password-cracking tool.
New hackers can practice using these tools in sandbox environments like TryHackMe or Hack The Box.
Becoming an ethical hacker involves structured learning, real-world practice, and official certification. Start with understanding networks, mastering Linux, and learning to code. Then practice with virtual labs and Capture The Flag (CTF) competitions.
Use resources like GitHub to build a portfolio, write technical blogs, and document your journey. Applying for internships or entry-level IT roles can help you gain experience while you learn.
Progress through certifications to demonstrate your expertise and break into high-paying roles.
Top Certifications for Ethical Hackers
Certifications validate your knowledge and prove your skills to employers. Here are the most recognized in 2025:
CEH: Ideal for beginners.
OSCP: Highly practical and respected.
CompTIA Security+: A solid foundation in cybersecurity.
PNPT: A newer hands-on cert gaining traction.
eJPT: Budget-friendly and beginner-friendly.
Each focuses on different aspects of ethical hacking, so choose based on your career goals.
Career Opportunities in Ethical Hacking
Cybersecurity is one of the fastest-growing fields, with over 3.5 million unfilled jobs projected by the end of 2025. Ethical hackers are in high demand across all industries.
Common job roles include:
- Penetration Tester
- Security Analyst
- Red Team Operator
- SOC Analyst
Use job boards like LinkedIn Jobs, Indeed, or CyberSecJobs to explore opportunities.
Average salaries range from $60,000 for entry-level positions to over $150,000 for senior roles.
Real-Life Case Studies and Success Stories
Ethical hacking saves companies millions by preventing data breaches. For instance, Apple offers up to $1 million for zero-day vulnerabilities. In 2016, Uber paid $100,000 to an ethical hacker who responsibly disclosed a critical flaw.
HackerOne reports that their hackers have collectively earned over $300 million for bug bounty programs. These examples highlight the importance and profitability of ethical hacking done right.
Legal and Ethical Aspects of Hacking
Ethical hacking must be conducted within legal boundaries. Unauthorized access, even with good intentions, is a crime.
Always ensure you have explicit permission before testing any system. Respect data privacy laws like GDPR and follow ethical frameworks provided by organizations such as NIST and OWASP.
Failure to do so can result in severe penalties, including imprisonment. Ethics and legality are what distinguish white-hat hackers from cybercriminals.
Conclusion

Ethical hacking is more than a career—it’s a mission to protect the digital world. If you’re passionate about cybersecurity, eager to understand how systems break, and committed to doing what’s right, this path is for you.
With the right knowledge, tools, and certifications, you can become a digital defender in 2025 and beyond. The world needs ethical hackers now more than ever.
So, are you ready to start hacking… ethically?







2 Comments
Reading this evokes the sense of opening a window after a storm. The air feels clearer, the perspective wider, and the heart lighter. It is both refreshing and grounding, restoring balance where it was missing.
Thank You so much for your kind reply