Ultimate Guide to Red Teaming in 2025: 10X Your Cybersecurity with Offensive Power

Table of Contents
ToggleWhat is Red Teaming?
Red Teaming is an advanced cybersecurity technique where professionals simulate the tactics, techniques, and procedures (TTPs) of real-world adversaries. The goal isn’t just to break in or exploit a system, but to test the effectiveness of an organization’s entire security infrastructure in a realistic, stealthy, and comprehensive way.
Unlike traditional vulnerability assessments or penetration tests, Red Teaming provides a full-scope attack simulation, often targeting people, processes, and technology. This allows organizations to identify blind spots and weaknesses that might never surface through routine scans. In 2025, Red Teaming is more crucial than ever as threat actors become more sophisticated and persistent.
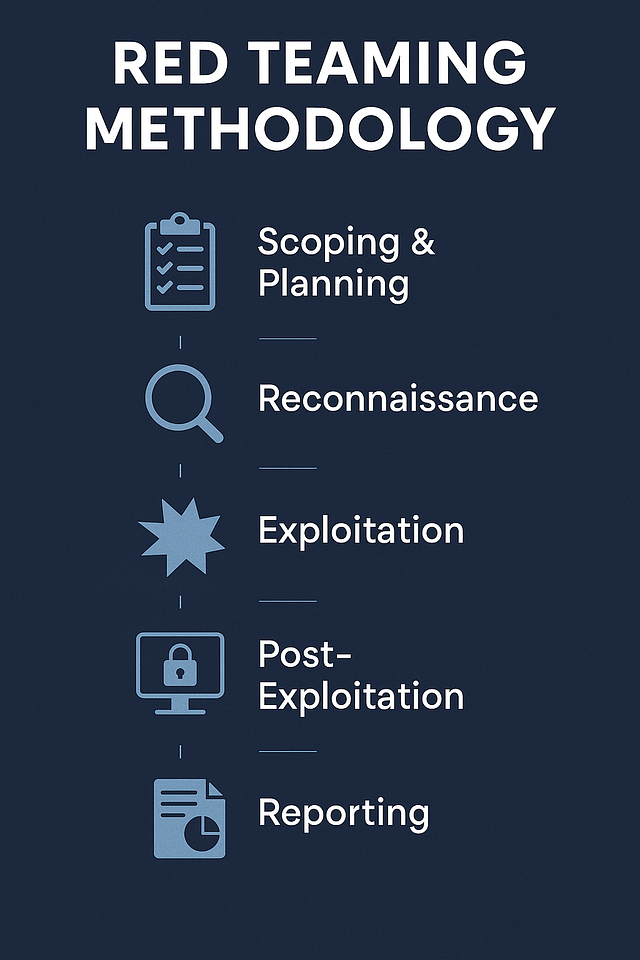
Red Teaming Methodology
A Red Team operation follows a detailed structure, mirroring the steps a real attacker would take. It begins with scoping and planning, where the team works closely with the client to define the rules of engagement. These rules clarify what systems can be tested, what techniques are off-limits, and how long the simulation will run.
Next comes reconnaissance. Red Teamers collect information using passive and active techniques—from open-source intelligence (OSINT) gathering to scanning for open ports or misconfigured services. This phase is critical because it sets the stage for targeted attacks.
Once enough data is collected, threat emulation begins. The team mimics adversaries, often using profiles from the MITRE ATT&CK framework. They might use phishing emails for initial access, escalate privileges using known exploits, and move laterally through a network.
Post-exploitation involves gathering evidence of compromise, maintaining access, and achieving specific goals, such as data exfiltration or domain dominance. Finally, the Red Team documents its findings, writes a comprehensive report, and conducts a debriefing session with the organization’s Blue Team and leadership to ensure that insights are translated into action.
Top Red Team Tools in 2025
Red Teamers rely on a wide arsenal of tools to simulate adversarial behavior effectively. In 2025, the go-to tools are more powerful and stealthy than ever.
Cobalt Strike remains a favorite for command and control operations, allowing attackers to manage compromised systems covertly. Metasploit Framework is used to develop and deploy custom payloads, giving Red Teamers a flexible platform to test vulnerabilities.
BloodHound is invaluable for mapping and exploiting Active Directory environments. By analyzing user and group relationships, it helps identify privilege escalation paths.
PowerShell-based tools like Empire and Covenant offer advanced post-exploitation capabilities, particularly useful in Windows-heavy environments.
Learning platforms like TryHackMe and Hack The Box have adapted their labs to include Red Teaming exercises, making them perfect for practice. Aligning tools and tactics with the MITRE ATT&CK framework ensures simulations are grounded in real-world threat intelligence.
Red Teaming vs Penetration Testing
While both Red Teaming and penetration testing aim to improve security, they differ greatly in scope, depth, and execution. Penetration testing is often compliance-driven, scoped to specific assets, and focused on identifying known vulnerabilities. It typically concludes with a list of findings and remediation suggestions.
Red Teaming, on the other hand, adopts the mindset of an adversary. It tests not only systems but also people and processes. Instead of scanning for weaknesses, Red Teamers exploit them, moving laterally through environments, evading detection, and achieving defined objectives. This approach validates the entire security posture, including incident response capabilities and detection tools.
Where a pentest might ask, “Is this system vulnerable to SQL injection?”, Red Teaming asks, “Can I access sensitive data, exfiltrate it, and avoid detection while doing so?”
| NO | Feature | Red Teaming | Penetration Testing |
|---|---|---|---|
| 1 | Objective | Emulate real-world attackers to test full defense stack | Identify and report known vulnerabilities |
| 2 | Scope | Broad: systems, people, and processes | Narrow: limited to specified systems or applications |
| 3 | Approach | Goal-oriented, stealthy, continuous | Checklist-driven, transparent |
| 4 | Execution Timeframe | Weeks to months | Hours to days |
| 5 | Techniques Used | Advanced persistent threat simulation, phishing, lateral movement | Advanced persistent threat simulation, phishing, lateral movement |
| 6 | Focus Area | Bypassing detection, measuring response capabilities | Identifying flaws and providing remediation steps |
| 7 | Tools | Cobalt Strike, BloodHound, Empire, MITRE ATT&CK | Nessus, Burp Suite, Nikto, Nmap |
| 8 | Blue Team Involvement | Often unaware (to simulate real breaches) | Typically aware and may assist in testing |
| 9 | Deliverables | Tactical and strategic insights, executive summary, improvement roadmap | List of vulnerabilities, risk levels, and fixes |
| 10 | Real-World Simulation | High - closely mirrors adversary behavior | Medium - limited to vulnerability discovery |
| 11 | Best For | Measuring detection and response, improving overall resilience | Measuring detection and response, improving overall resilience |
| 12 | Regulatory Fit | Ideal for internal readiness assessments | Often required for compliance (PCI-DSS, ISO 27001, etc.) |
| 13 | Cost | Typically higher due to duration and complexity | Lower, shorter engagement and resource use |
Legal and Ethical Side of Red Teaming
Red Teaming involves simulating real attacks, which means it can easily cross ethical or legal boundaries if not handled correctly. That’s why it’s essential to operate within strict guidelines.
Before any test begins, Red Teams must work with organizations to sign a clear Rules of Engagement (ROE) document. This ensures all parties understand what systems are in scope and sets clear expectations for behavior during the test. Having proper authorization from executives protects both the team and the client from legal fallout.
It’s also vital to ensure compliance with regulations like GDPR and HIPAA, especially when handling sensitive personal or health-related information. Ethical Red Teamers avoid any actions that could harm users, destroy data, or affect operations. The goal is to make security better—not to create chaos.

Careers and Certifications in Red Teaming
If you’re considering a career in Red Teaming, you’re stepping into one of the most elite and rewarding areas in cybersecurity. Red Teamers are highly skilled professionals who must think creatively, stay up to date with evolving threats, and know how to simulate them safely.
To get started, you’ll need foundational knowledge in networking, systems, and scripting. Skills like exploit development, lateral movement, and social engineering are must-haves. Familiarity with Active Directory, Windows internals, and PowerShell scripting gives you a serious edge.
Certifications help validate your skills and open doors:
OSCP (Offensive Security Certified Professional) teaches real-world exploitation and reporting.
CRTO (Certified Red Team Operator) focuses on command and control infrastructure.
PNPT (Practical Network Penetration Tester) is excellent for beginners wanting hands-on learning.
CRTP (Certified Red Team Professional) deep dives into Windows enterprise environments and domain attacks.
These credentials are recognized globally and signal that you’re ready for serious offensive work.
How to Build a Red Teaming Lab
Nothing beats hands-on experience, and a home lab is the best way to learn Red Teaming without risking live systems. Thankfully, you don’t need expensive equipment to get started.
Begin with virtualization platforms like VirtualBox or VMware. Install Kali Linux as your attacking machine and set up vulnerable environments using Metasploitable or Windows VMs. Configure a basic Active Directory environment to simulate enterprise networks.
Once your lab is set, practice common attack paths: perform reconnaissance, gain initial access, escalate privileges, and move laterally. Tools like Mimikatz, Responder, and SharpHound can help you experiment with real TTPs in a controlled environment.
Online platforms like TryHackMe and Hack The Box offer Red Team labs tailored for every skill level. They guide you through realistic scenarios and help you build confidence before entering the field.
Why Businesses Need Red Teaming
Red Teaming isn’t just for tech giants or government agencies. Every business that stores data, processes transactions, or operates in a digital environment can benefit from Red Team simulations.
These exercises reveal blind spots that standard audits or compliance tests may miss. They provide insight into how attackers think and show whether the organization’s defenses, detection tools, and incident response teams are truly effective.
Red Teaming also boosts the capabilities of Blue Teams by giving them real-world scenarios to learn from. It encourages collaboration, continuous improvement, and a culture of security awareness that touches every department.
A great example is Microsoft, which regularly runs internal Red Team engagements to test its systems and train its defenders. The result? Stronger defenses and faster response times.
Conclusion + Resources
In the evolving landscape of cybersecurity, Red Teaming has become not just a luxury, but a necessity. It transforms the way organizations think about security—from compliance checkboxes to active defense strategies.
If you’re a cybersecurity professional looking to level up or an organization seeking to validate your defenses, Red Teaming is your next big move. Build your lab, sharpen your skills, and explore certifications that will set you apart in the industry.
Ready to act like an adversary to become a better defender? Start today, and turn your cybersecurity strategy from passive to powerful.
Read More