Red Teaming vs Blue Teaming: 2025’s Ultimate Cybersecurity Showdown [Complete Guide]
![Red Teaming vs Blue Teaming: 2025’s Ultimate Cybersecurity Showdown [Complete Guide]](https://mlyjmfwz2wt8.i.optimole.com/cb:-MVX.443/w:1024/h:764/q:mauto/rt:fill/g:ce/ig:avif/https://hackinglovers.com/wp-content/uploads/2025/06/ChatGPT-Image-Jun-21-2025-07_24_46-PM.png)
While one side attacks your digital defenses with hacker-like precision, the other protects your systems like a fortress of firewalls. But this isn’t just a game of offense and defense (Red Teaming vs Blue Teaming) — it’s the heart of modern cybersecurity strategy.
According to IBM’s 2024 report, companies that actively engage in red and blue teaming reduce breach costs by 60% — that’s huge. If you’re diving into cybersecurity, it’s essential to know which side of this digital war you want to be on.
In this guide, we’ll cover the complete breakdown of Red Teaming vs Blue Teaming, their tools, goals, real-world examples, and how to choose the right path.
Table of Contents
ToggleWhat is Red Teaming?
Red Teaming is all about thinking like the enemy. It’s an offensive cybersecurity practice where experts simulate real-world attacks to test an organization’s defenses.
Focus: Offense, simulation of real attacks
Key Roles: Ethical hackers, penetration testers, red team operators
Tools: Metasploit, Sliver, Mythic, Cobalt Strike
Objective: Identify vulnerabilities before malicious hackers do
Method: Social engineering, phishing, lateral movement, and custom exploit chains
Red Teaming is stealthy, goal-oriented, and often unannounced to the Blue Team. Think of it as a high-stakes cyber drill.
Blue Teaming is your cyber bodyguard. It involves monitoring, detecting, and responding to threats to protect the organization’s digital assets.
Focus: Defense, prevention and response
Key Roles: SOC analysts, forensic investigators, threat hunters
Tools: Splunk, Wireshark, Zeek, Velociraptor, Microsoft Sentinel
Objective: Detect, block, and respond to cyber threats in real time
Method: SIEM monitoring, threat intelligence, incident response, and endpoint security
Blue Teams work continuously to harden systems, review logs, respond to alerts, and ensure compliance.
Red Teaming vs Blue Teaming: Key Differences
| NO | Feature | Red Teaming | Blue Teaming |
|---|---|---|---|
| 1 | Mindset | Offensive | Defensive |
| 2 | Goal | Simulate real-world attacks | Detect and respond to real threats |
| 3 | Approach | Stealthy and proactive | Reactive and continuous |
| 4 | Tools Used | Often unknown to Blue Team | Splunk, Sentinel |
| 5 | Visibility | Often unknown to Blue Team | Always-on |
| 6 | Outcome | Report vulnerabilities | Prevent data breaches |
Red Team Tools & Tactics in 2025
In 2025, Red Teams are more sophisticated than ever, leveraging both open-source and commercial tools.
Cobalt Strike: Advanced post-exploitation and beaconing tool
Metasploit: Exploitation framework
Mythic C2: Command and control for adversary emulation
Empire/Sliver: Post-exploitation frameworks
Tactics: Social engineering, phishing emails, privilege escalation, pivoting across networks
Red Teamers focus on creativity — they mimic real APT groups and test every layer of defens

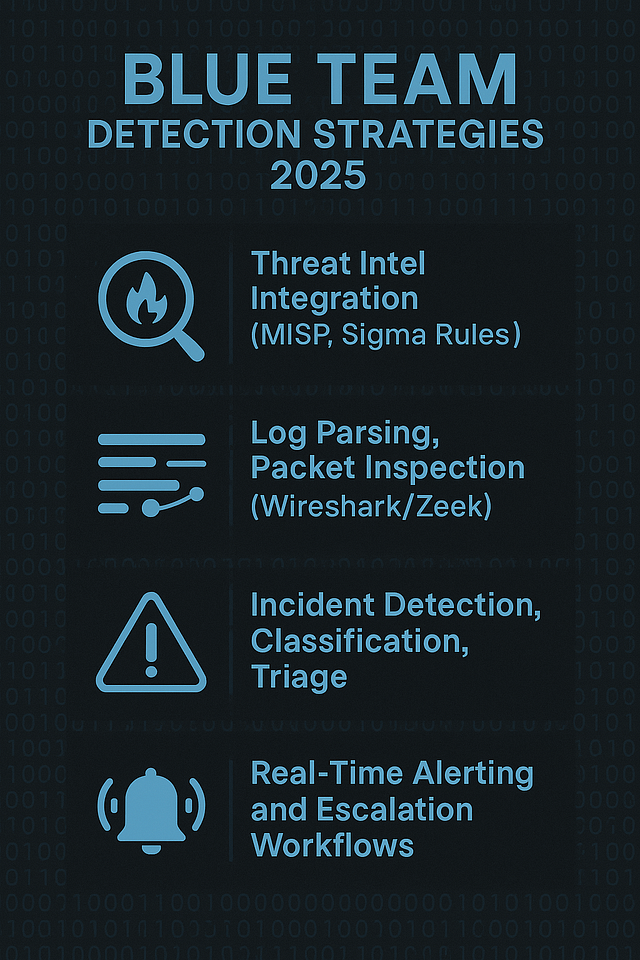
Blue Team Detection Strategies (2025)
Blue Teams now operate with cutting-edge visibility into endpoints, networks, and the cloud.
SIEM Integration: Using Splunk, ELK, or Sentinel to centralize log data
Endpoint Monitoring: Tools like Velociraptor and CrowdStrike
Threat Intelligence: Real-time threat feeds and IOC correlation
Detection Frameworks: MITRE ATT&CK, Sigma Rules, YARA signatures
Blue Teams are no longer just responders — they’re proactive hunters.
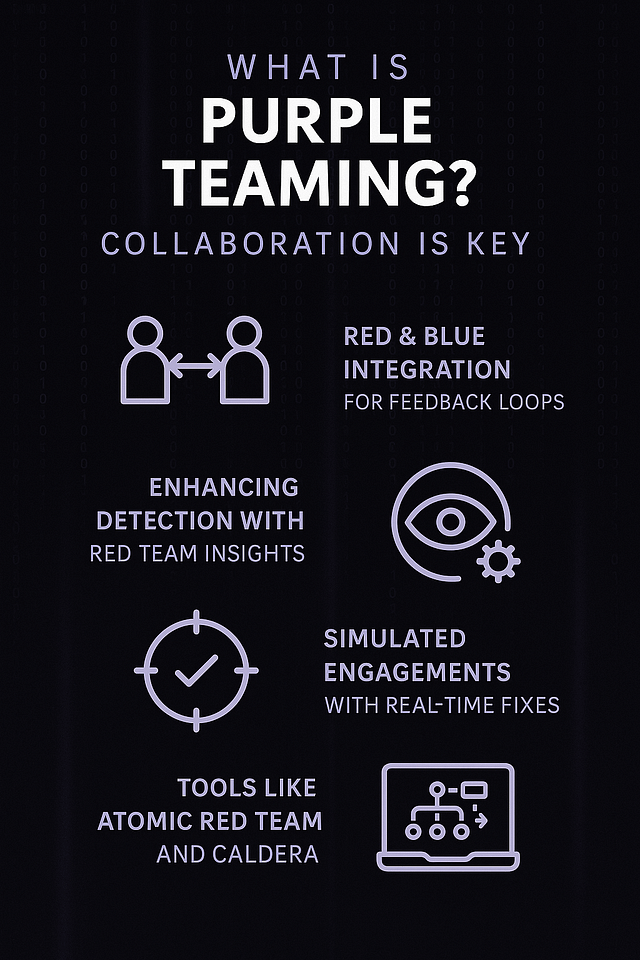
What is Purple Teaming? Collaboration is Key
Purple Teaming bridges the gap between Red and Blue.
Goal: Improve effectiveness through collaboration
Process: Red Team simulates, Blue Team observes, both improve
Tools: Atomic Red Team, Caldera, PlexTrac
Benefits: Real-time feedback, stronger detection rules, faster response times
Purple Teams represent a shift toward unified cybersecurity strategies.
Career Guide – Red Teaming vs Blue Teaming
Red Team:
Certifications: OSCP, CRTP, CEH, PNPT
Skills: Exploitation, scripting, lateral movement, social engineering
Ideal for: Creative minds, offensive thinkers
Blue Team:
Certifications: CompTIA CySA+, GCIA, GCFA, CHFI
Skills: Detection engineering, SIEM management, forensic analysis
Ideal for: Analytical thinkers, defenders, incident handlers
In 2025, both roles are in high demand with salaries ranging from $70k to $160k+.
Real-World Examples of Red Teaming vs Blue Teaming
Capital One Simulation (2022): Red Team mimicked an APT-style attack which exposed IAM misconfigurations. Blue Team later built tighter AWS policies.
SolarWinds Breach Response: Blue Team detected unusual outbound traffic using NetFlow and halted lateral movement.
Banking Sector Drill: Red Team created a physical breach scenario; Blue Team activated building access logs to trace.
These examples show how essential both sides are.
Red Teaming vs Blue Teaming – Which is Right for You?
Are you a builder or a breaker?
Do you enjoy exploiting systems or protecting them?
Red Team = thrill, creativity, challenge
Blue Team = responsibility, depth, vigilance
Try both using platforms like TryHackMe and BlueTeamLabs.
Final Thoughts
Whether you’re drawn to Red Teaming’s thrill or Blue Teaming’s vigilance, both paths are essential to a secure digital future. They’re not enemies — they’re partners in protection. And if you want the best of both worlds? Go Purple!
Explore our in-depth guides to get started:





1 Comment
Perfect piece of work you have done, this internet site is really cool with good info .